I just love it how old news are recycled with a bit of a flare when they become relevant again. The latest Orkut worm reports talk about the technique that the worm writer has used to distribute its code. Quoting from the original article above: “It then downloads and executes a heavily obfuscated JavaScriptâ€â€¦ looking at the code, I was expecting some whiz-bang brand-spankin-new cool-as-ice JS that you can’t even watch without eye protection. Alas, I was greeted with the good-ole’ “packed†obfuscation (see pdp’s post in it):
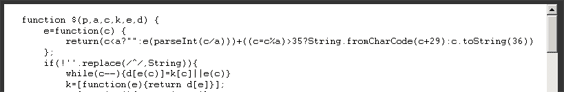
This brings us back to our August post on obfuscators (that are obviously easily detected and processed by us) which talked about the “packed†strand of JS obfuscation…
Hope that the industry will bring in something more exciting in the next wave of malicious code 😉
Leave a Reply