While conducting research for the latest Malicious Page of the Month we have just released, we tried to track down the origins of the crimeware.
Obviously, this is a daunting task by itself, and although sometimes security researchers are able to point at specific people as the ones running the criminal activity, it does not always help that much (remember the RBN case where multiple law enforcement agencies were notified, but the people behind the scenes were never arrested or indicted).
Well then, back to our little server – the domain name hosting the crimeware (Neosploit 2.0.13) was hosted in Hong-Kong (see below)
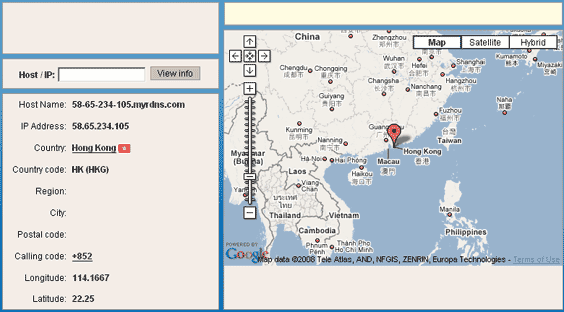
So that does not bring us any closer to who is this – as the address is located at a hosting company. Fortunately, our research brought in some additional IP addresses. We managed to grab these from the web server just like we have uncovered the 8,700 FTP account credentials that the research paper talks about (no exploits or attacks were used to do so – simply thinking outside the box sufficed).
Tracking these down proved to be a nice tour around the globe (long whois info deprecated for clarity):
| inetnum:Â Â Â Â Â Â Â 78.109.19.160 – 78.109.19.167
netname:Â Â Â Â Â Â Â activebill descr:Â Â Â Â Â Â Â Â Â activebill – Andrey Smirnov person:Â Â Â Â Â Â Â Â Andrey Smirnov address:Â Â Â Â Â Â Â 125167, Leningradsky prospekt, 47, Moscow, Russia remarks:Â Â Â Â Â Â Â phone:Â Â Â Â Â Â Â +7 095 795 0295 phone:Â Â Â Â Â Â Â Â Â +7 495 795 0295 remarks:Â Â Â Â Â Â Â fax-no:Â Â Â Â Â Â +7 095 795 0295 fax-no:Â Â Â Â Â Â Â Â +7 495 795 0295 nic-hdl:Â Â Â Â Â Â Â AS32250-RIPE e-mail:Â Â Â Â Â Â Â Â admie@svetcorp.net source:Â Â Â Â Â Â Â Â RIPE # Filtered |
inetnum:Â Â Â Â Â Â Â 82.146.40.0 – 82.146.47.255
netname:Â Â Â Â Â Â Â ISPSYSTEM descr:Â Â Â Â Â Â Â Â Â ISPsystem at MSM country:Â Â Â Â Â Â Â RU admin-c:Â Â Â Â Â Â Â DS2036-RIPE tech-c:Â Â Â Â Â Â Â Â AB11726-RIPE status:Â Â Â Â Â Â Â Â ASSIGNED PA mnt-by:Â Â Â Â Â Â Â Â ISPSYSTEM-MNT source:Â Â Â Â Â Â Â Â RIPE # Filtered <>person:Â Â Â Â Â Â Â Â Dmitry Sidorovaddress:Â Â Â Â Â Â Â PoBox 30, 664017, Irkutsk, Russia phone:Â Â Â Â Â Â Â Â Â +7 495 727 38 79 e-mail:Â Â Â Â Â Â Â Â inet@ispserver.com nic-hdl:Â Â Â Â Â Â Â DS2036-RIPE source:Â Â Â Â Â Â Â Â RIPE # Filtered person:Â Â Â Â Â Â Â Â Alexandr Brukhanov address:Â Â Â Â Â Â Â PoBox30, 664017, Irkutsk, Russia phone:Â Â Â Â Â Â Â Â Â +7 495 727 38 79 nic-hdl:Â Â Â Â Â Â Â AB11726-RIPE source:Â Â Â Â Â Â Â Â RIPE # Filtered |
inetnum:Â Â Â Â Â Â Â 85.17.111.0 – 85.17.111.255
netname:Â Â Â Â Â Â Â LEASEWEB descr:Â Â Â Â Â Â Â Â Â LeaseWeb descr:Â Â Â Â Â Â Â Â Â P.O. Box 93054 descr:Â Â Â Â Â Â Â Â Â 1090BB AMSTERDAM descr:Â Â Â Â Â Â Â Â Â Netherlands descr:Â Â Â Â Â Â Â Â Â www.leaseweb.com remarks:Â Â Â Â Â Â Â Please send email to “abuse@leaseweb.com” for complaints remarks:Â Â Â Â Â Â Â regarding portscans, DoS attacks and spam. remarks:Â Â Â Â Â Â Â INFRA-AW country:Â Â Â Â Â Â Â NL admin-c:Â Â Â Â Â Â Â LSW1-RIPE tech-c:Â Â Â Â Â Â Â Â LSW1-RIPE status:Â Â Â Â Â Â Â Â ASSIGNED PA mnt-by:Â Â Â Â Â Â Â Â OCOM-MNT source:Â Â Â Â Â Â Â Â RIPE # Filtered |
| OrgName:Â Â Â Galaxyvisions Inc
OrgID:Â Â Â Â Â GALAX-6 Address:Â Â Â 882 3rd avenue 8th floor City:Â Â Â Â Â Â Brooklyn StateProv:Â NY PostalCode: 11232 Country:Â Â Â US |
||
Putting all these guys on the map results in a very interesting “international man of mystery†cross-continent network of connections:
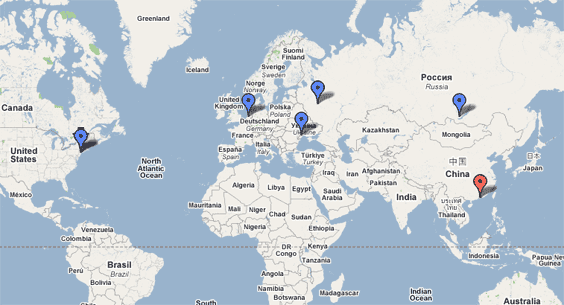
Obviously we are looking at some eastern-bloc oriented operation, with some access to resources in the Netherlands and the US (either other people, or just computers from which access could have been made).
Now that law enforcement agencies are involved with this, maybe we would see some developments on the matter, although from the looks of these pins on the map, I expect some really interesting multi-lingual cop-speak to spur out soon…
Leave a Reply